Wide area distributed corporate networks have become widespread among companies with a few local offices, as well as companies with multiple branches throughout the country or all over the world.
At its core, the main purpose of any information network is to deliver data (content) to the recipient (user) with a guaranteed quality of services, including bandwidth, delay and allowable limit of delay variation. However, with the current growth in the number of users, applications and the amount of content they consume (traffic), it is becoming increasingly difficult to ensure the quality of network services. The use of legacy technologies to build connections between autonomous systems with different internal routing, technical and logical segments is a major challenge and drawback of global data networks. The consequences are a decrease in the speed of information transmission, the presence of large non-useful data overhead on packets traversing the networks that lead to inefficient use of network bandwidth, significant increase in network delays, lower quality of end user experience, etc.
A computer network administrator today faces multiple challenges with configuring and operating a computer network. This is true whether the administrator is operating the network to support the business of a corporate office, the production and distribution of rich digital media, the transmission of live content from an event, the operation of a voice-over-internet protocol telephone network, a video conference network or any other network of two or more connected devices.
The administrator faces the challenges of connecting and managing devices used to transport traffic across the network in a manner that allows for monitoring of the network operation, avoiding loops in the network, maximizing traffic throughput, minimizing latency, reducing jitter, enhancing security, and efficiently updating the network topology and devices in the network. In the case of enterprise networks, support is also required for a diverse range of digital devices: workstations, stationary computers, tablets, mobile phones, video surveillance systems, information kiosks, etc., working on specialized protocols of radio communication, data transmission, and configuration requirements at the physical network device level.
From the network administrator’s perspective, all of these different devices that work on different technologies have to be managed centrally, the information on the network must be transmitted encrypted, and the network must be resilient. This process is expensive and time-consuming to the enterprise.
Various solutions have emerged along the way to these networking problems.
The virtual private network (VPN) market has been one of the fastest growing data services due to its relevance to the enterprise market (for collaboration applications, private cloud environments, etc.) and its use in the network operator market (in particular, in the construction of network infrastructure during the deployment of LTE and the organization of high-speed connections to provide connections in the data center).
But they drive contradictory objectives: the enterprise user seeks to isolate its VPN from VPNs of other enterprises, whereas the network operators are focused on enabling the maximum connectivity across all network by distributing routing protocols such as BGP, OSPF, IS-IS, RIP over its composite information network.
With this mechanism, each network router creates a routing table that shows the path of packages to each of the networks included in the composite network. The provider can abandon the IP protocol to aggregate an enterprise user’s sites alone, through use of other protocols such as frame relay and ATM.
But then the ability to provide IP services to the client is lost, which in modern conditions practically devalues the service provided. Providers can of course support different sets of services using different protocols (as many providers do), but this is not the best solution; a mixture of protocols creates a lot of difficulties for both the client and the provider.
Complicating this situation is that a network built with components from different manufacturers and services provided by different providers is harder to monitor and manage centrally.
Another popular approach has been the use of multi-protocol switching by tags (MPLS). This approach is an expensive undertaking for an enterprise. In addition, MPLS introduces challenges when trying to connect remote workplace in another country.

More recently, Software Defined WAN (SD-WAN) technology has been developed for more efficient use of communication channels. It uses software-defined networks (SDN) to find the most efficient way to route and manage traffic.
SD-WAN solutions vary from vendor to vendor, but most of them support hybrid global networks-dynamic routing of traffic over private and public networks, such as MPLS. A provider can use existing well-known technologies and protocols to implement SD-WAN.
SD-WAN has a huge number of advantages over traditional technologies, but also has a sufficient number of disadvantages. All these disadvantages are primarily related to the use of traditional data transfer protocols. Solutions from different SD- WAN providers are not compatible.
This means that changing them freely when necessary is not an easy task.
When a user uses an SD-WAN solution, the operator on whose reference network the user is based has difficulty managing the routing of its own network because the user uses its own tunnel routing table created by the SD-WAN solution.
This, in turn, leads to a “bottleneck” on the operator’s nodes, and as a result, data transmission is slowed down for both the user and the operator. In addition, users of network data services suffer when there is inadequate data throughput, too much latency or jitter, or potential data vulnerabilities across a computer network. sers can experience long download times for content files, jumpy streaming media experiences, dropped voice phone calls, blurry video images, re-transmission of dropped or affected data packets, and leakage of data (e.g., data about the websites they visit).
Accordingly, there is a need in the art for a fundamentally new logical networking system and a fundamentally new method of processing data packets that can operate using existing physical communication channels and that can guarantee the quality of services (increased data throughput, reduced latency, limited jitter, enhanced data security, support for all devices attached to the network, simplified true end-to-end network configuration and administration, true centralized network monitoring, and reduced cost of network operation), while also improving users’ data experience.
At the same time, communication and information exchange on strategically important objects is possible only through the Internet and IP technologies.
Multi Service Tunnel Network Technology
MSTNT platform is based on Multi-Platform Tunnel OS (MPT OS), which is installed on any modern telecommunications equipment, implemented on processors with X86, ARM, MIPS architecture. This allows you to create a distributed corporate networks of varying complexity and cost of implementation, but with the same level of technological solutions and security.
MSTN technology was developed using a completely new architecture, which overcomes all the existing disadvantages and limitations of traditional network solutions.
MSTNT uses a new packet header structure and generalized address information to route packet traffic across the network independently of TCP/IP.
MSTNT allows you to create monolithic links from multiple IP transport links by summing the bandwidth of individual subchannels, while maintaining the order of delivery of isolated packets.
Subscriber Autonomous System.
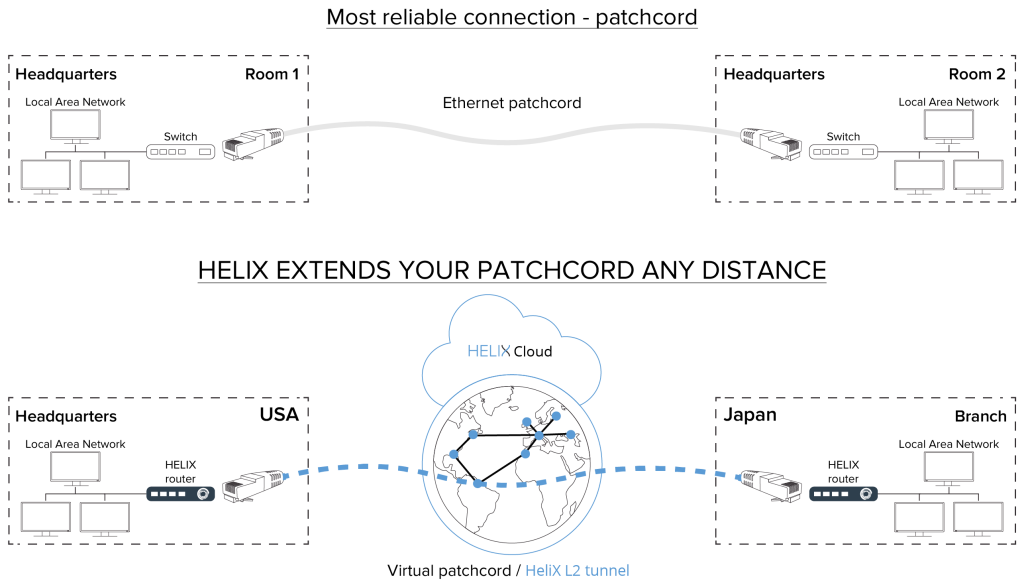
The Autonomous System is built on top of any channel, be it a dedicated line or the Internet, abstracting routing technologies and physical devices and allows creating logical connections in which traffic can be managed as desired, creating isolated monolithic communication channels from multiple transport IP channels from the data center to connected remote branch offices.
Autonomous System (AS) has all the necessary tools to manage and monitor, diagnose and control all processes occurring in the network, both from the user side, and from the operator’s or provider’s side.
To build the AS there is no need to purchase specialized equipment of any particular manufacturer, which significantly reduces the cost of organizing the network at the initial stage and allows you to freely change equipment during subsequent operation or expansion of the network, thereby significantly reducing the cost of ownership of the network.
Control and monitoring system allows network administrators to centrally manage the network, configure and monitor communication channels in real time.
Telecom operators and service providers, whose backbone network hosts AS users, get a possibility to avoid a “bottle neck” by means of using reflectors in their network that dynamically redirect traffic to the best path.
Combined with hot redundancy and data corruption protection in case of emergencies and unplanned situations, it allows packets to be delivered in the shortest possible way, while the MSTNT monitoring and diagnostics system will identify and find the cause, and then pass the data collected about the failure to the personnel responsible for the emergency section of the network.
From a technological point of view, the Autonomous System-based solutions are simple and reliable, and the standardized configuration allows to implement any requirements of the corporate customer.
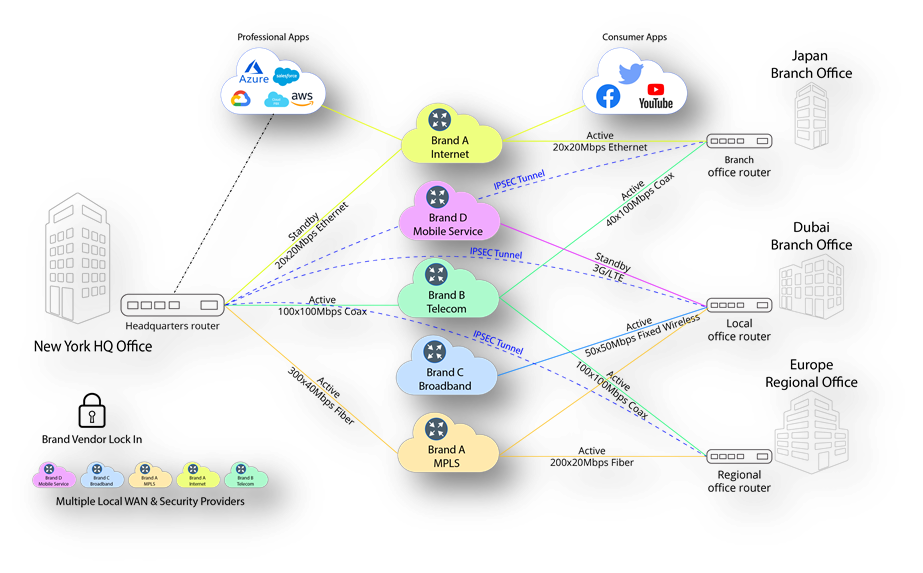
Each subscriber terminal in the standard configuration is capable of:
simultaneously work with several independent Internet channels in summation mode, redundancy (hot and cold) while transmitting six independent L2 channels, and the resulting L2 Ethernet transport can transmit packets both with and without VLAN 802.1Q technology (single TAG, QinQ).
(in other words: each subscriber terminal in a standard configuration, is capable of connecting six independent L2 links between terminals, it’s a patchcord between users’ computers, with all the advantages of a local network… no losses, packet sequence recovery, etc. regardless of their location.
In this case, unlike TCP (which sends a packet to nowhere via a route and waits for confirmation of delivery or resend), MSTP constantly “knows” the real state of the route to the destination at the moment and always has a few spare routes).
Customer technicians are able to segment all services, presenting each service as a simple peer-to-peer network, avoiding the use of different protocols and technologies. This simplifies management and monitoring, allows problem areas to be identified as quickly as possible and eliminates the need to create intricate routing webs when emergencies occur.

Instead of using several different protocols and technologies from different vendors, the technician receives a multifunctional powerful toolkit that allows any modern equipment from different vendors, in real time through a centralized management interface (MMI), to load, save, edit, automatically generate configuration files as a server (collector) and client part for each tunnel.
Also evaluate the quality of each tunnel and all its subchannels and their performance when loaded with useful data, as well as provide visibility into the status of physical connections, logical channels and the state of the border equipment.
This makes it possible to implement all modern requirements of the enterprise sector on a single technology platform in a single solution, taking into account any number of summarized and reserved links from different service providers.
Even when using a lossy channel, the MSTNT makes it possible to significantly improve the quality of communication: eliminate losses and minimize jitter.
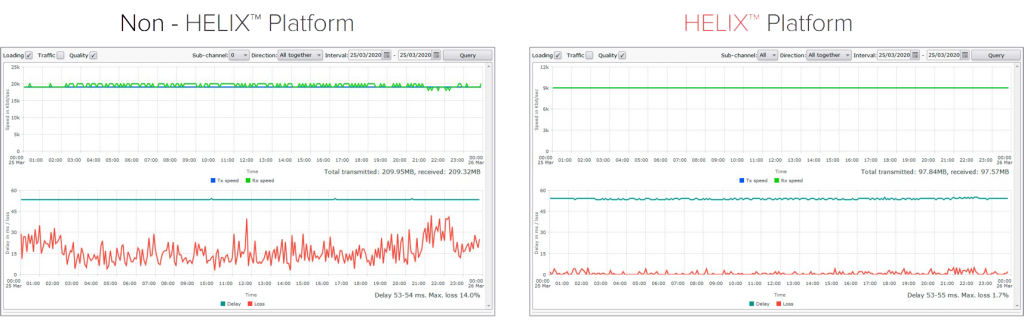
To summarize the above, it is clear that the Autonomous System is fault-tolerant and has all the necessary functionality to control and monitor all the processes occurring in the network.

